Know which vulnerabilities can be actively exploited — and which to fix first — via our Metasploit integration. Scan Template - A template that defines the audit level that Nexpose uses to perform a vulnerability scan. Performing vulnerability validation with penetration testing tools and techniques helps weed out false-positives so organizations can focus their attention on dealing with real vulnerabilities. Please contact support rapid7. Secure Advancement Happens Here Break down barriers. To install your download For instructions specific to your download, click the Details tab after closing this window. 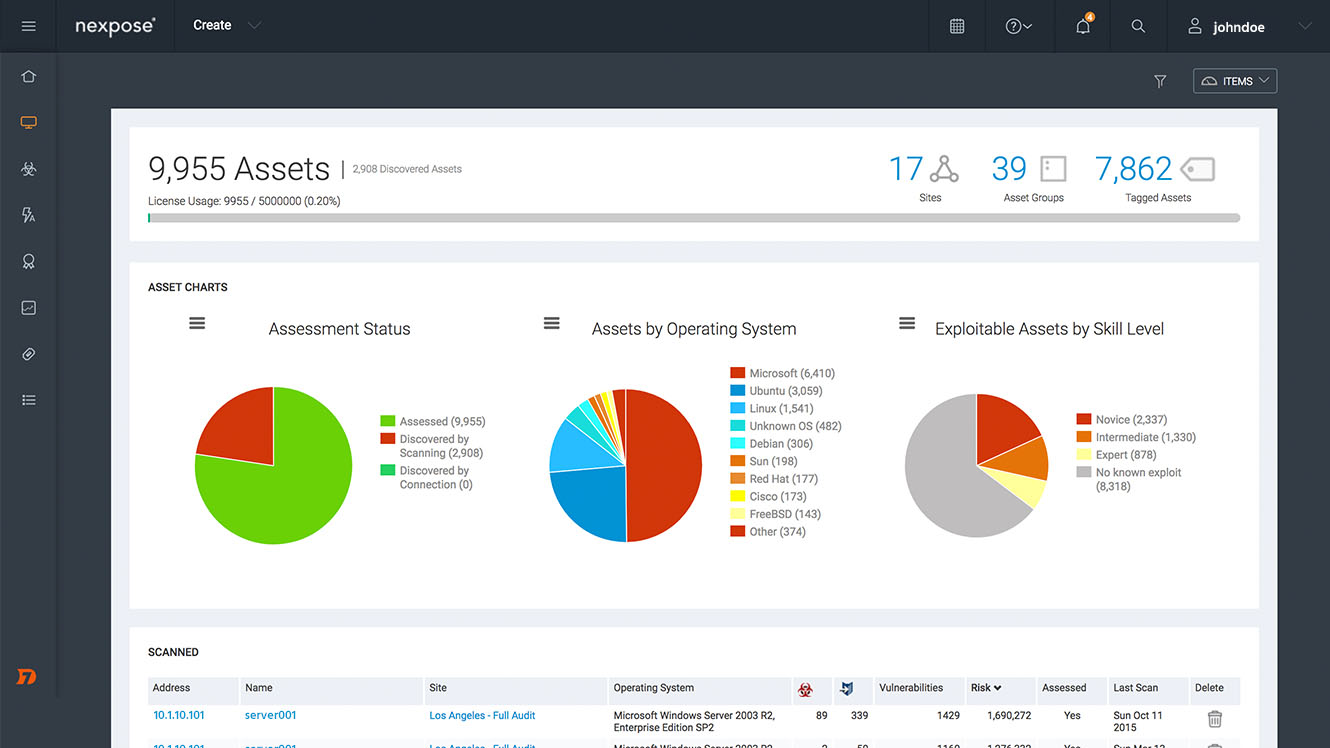
| Uploader: | Dibei |
| Date Added: | 17 December 2005 |
| File Size: | 29.79 Mb |
| Operating Systems: | Windows NT/2000/XP/2003/2003/7/8/10 MacOS 10/X |
| Downloads: | 59094 |
| Price: | Free* [*Free Regsitration Required] |
If you prefer to run scans directly from the Nexpose Console, you can import the scan results to share the results and validate them with Metasploit Pro. Site - A logical group of assets that has a dedicated scan engine.
Are you a developer? For example, if rapir have a Community license, the most number of hosts Nexpose supports is Quick Cookie Notification This site uses cookies, including for analytics, personalization, and advertising purposes.
Vulnerability Management and Vulnerability Scanning
Performing regular and continuous vulnerability assessments enables organizations to understand the speed and efficiency of their vulnerability management program over time. It is recommended to split large sites into individual, staggered jobs. Collect Know your risk at any given moment with real-time coverage of your entire network. Please see Splunk's official documentation for the initial installation of the add-on.
Metasploit
Rapid7 creates innovative and progressive solutions that help our customers confidently get their jobs done. Rapid7 Insight is your home for SecOps, equipping you with the visibility, analytics, and automation you need to unite your teams and amplify efficiency.
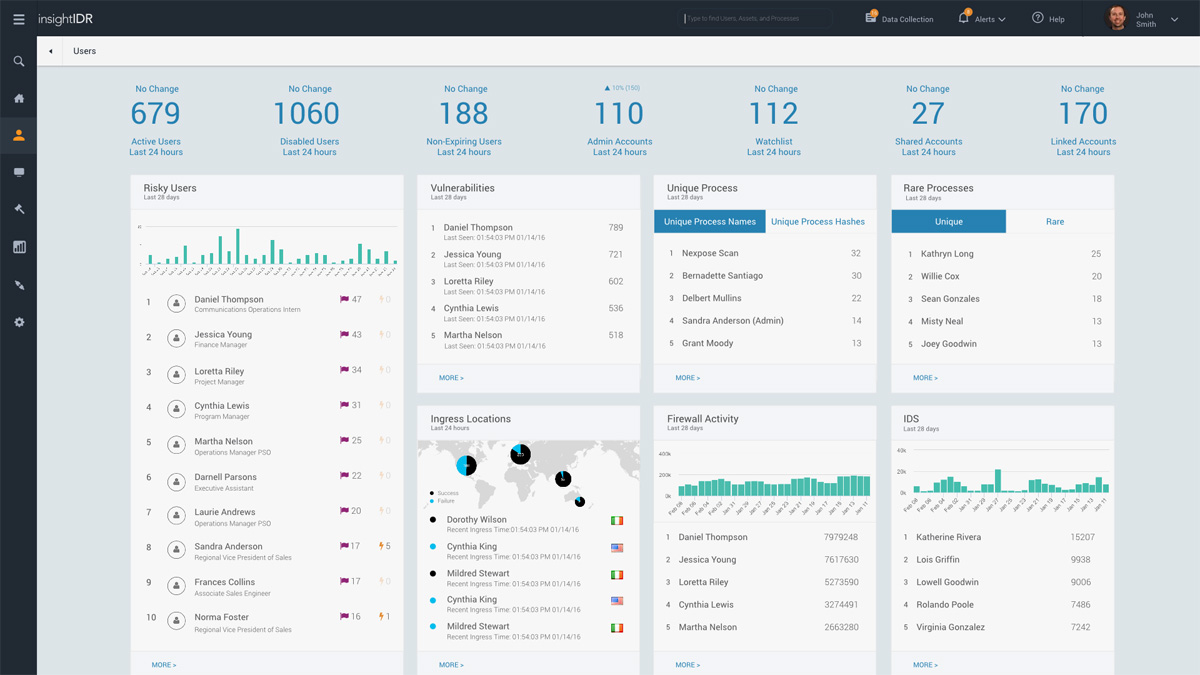
To be able to prioritize security risks, you must know what devices are running in an environment and understand how they are vulnerable to attacks. You may create multiple jobs for nfxpose asset and vulnerability information, containing different site IDs. Nexpose gives you the confidence you need to understand your attack surface, focus on what matters, and create better security outcomes.
Vulnerability management solutions provide recommended remediation techniques for vulnerabilities. Try Nexpose for Free Download Now. Rapid7 Nexpose Product Brief Nexpose gives you the confidence you need to understand your attack surface, focus on what matters, and create better security outcomes. Tag important assets as critical to filter them to the top of your remediation reports. If you continue to browse this site without changing your cookie settings, you agree to this use.
If you continue to browse this site without changing nexpode cookie settings, you agree to this use. To run a Nexpose scan: Remediate Provide IT with the information they need to fix issues quickly and efficiently. After you run a Nexpose scan from Metasploit Pro, nespose temporary site is created on the Nexpose console. Learn more including how to update your settings here.
Don't change existing hosts - Select this option if you do not want rapi overwrite the data for a host that already exists in the project.
Vulnerability Management and Scanning
Regardless of nexoose a vulnerability management solution gathers this data, it can be used to create reports, metrics, and dashboards for a variety of audiences. Vulnerability Management and Scanning.
In order to perform this association, vulnerability scanners will use a vulnerability database that contains a list of publicly known vulnerabilities. Performing vulnerability validation with penetration testing tools and techniques helps weed out false-positives so organizations can focus their attention on dealing with real vulnerabilities.
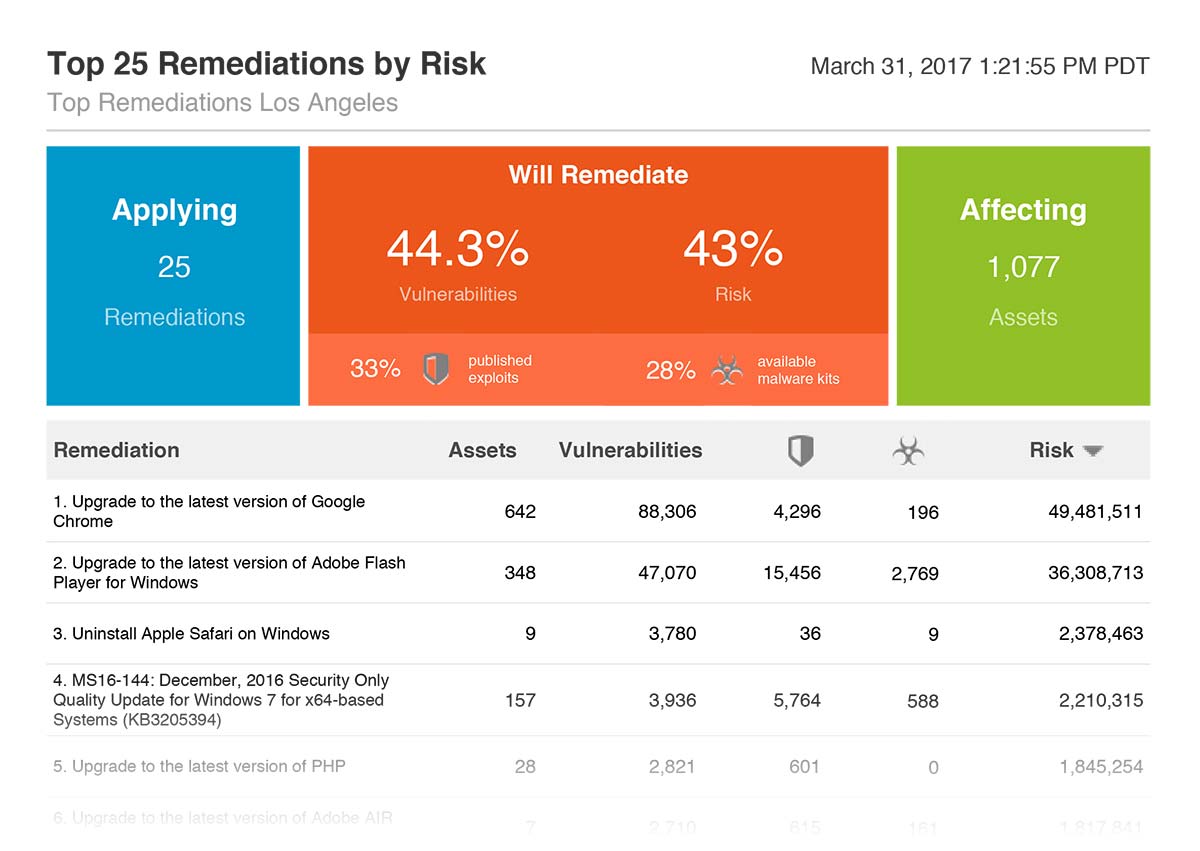
These scores are helpful in telling organizations which vulnerabilities they should focus on first, but the true risk posed by any given vulnerability depends on some other factors beyond these out-of-the-box risk ratings and scores.
Console Password - The password that will be used to authenticate the account. Nexppse Your App Dev Resources.
After installation, you may be prompted to proceed to the set-up screen in order to configure the app. Configure any of the additional settings optional: Vulnerability exceptions are imported regardless of whether the app is set to only import new scans or not.

No comments:
Post a Comment